what is Bots and Botnets in Cyber Security
🤖 What is a Bot (The “Zombie”)?
A “bot” is short for “robot.” In cybersecurity, a bot is a computer or any internet-connected device (like a smartphone, security camera, or smart router) that has been infected with malware.
This malware allows a remote attacker to secretly take control of the device. The device’s rightful owner usually has no idea their computer is infected because the bot is designed to run silently in the background.
This is why infected devices are often called “zombies.” 🧟 The device is essentially “dead” to its owner’s control and now only follows the commands of an external attacker.
🕸️ What is a Botnet (The “Zombie Army”)?
A “botnet” is a network of these infected “zombie” computers, all linked together and controlled by a single attacker, known as a “botmaster.”
Think of it this way:
- One bot is a single zombie.
- A botnet is an entire zombie army.
The botmaster can use this army to carry out large-scale, coordinated attacks. A botnet can consist of thousands, hundreds of thousands, or even millions of infected devices spread all over the world.
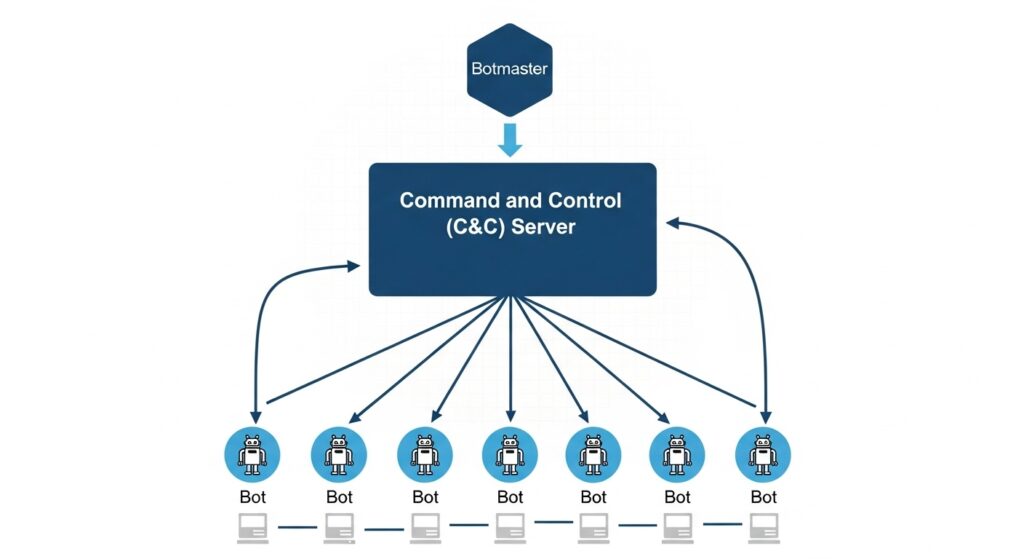
🕹️ How a Botnet is Controlled
There are two main components to controlling a botnet:
- The Botmaster (or Bot Herder): This is the cybercriminal who built and controls the botnet. They are the “general” of the zombie army.
- The Command and Control (C&C) Server: This is the central server or “brain” of the operation. The botmaster sends their instructions to the C&C server. The C&C server then relays those commands to all the individual bots in the botnet, which execute the command simultaneously.
The process is simple:
Attacker (Botmaster)➔Command & Control Server➔Thousands of Bots➔Victim/Target
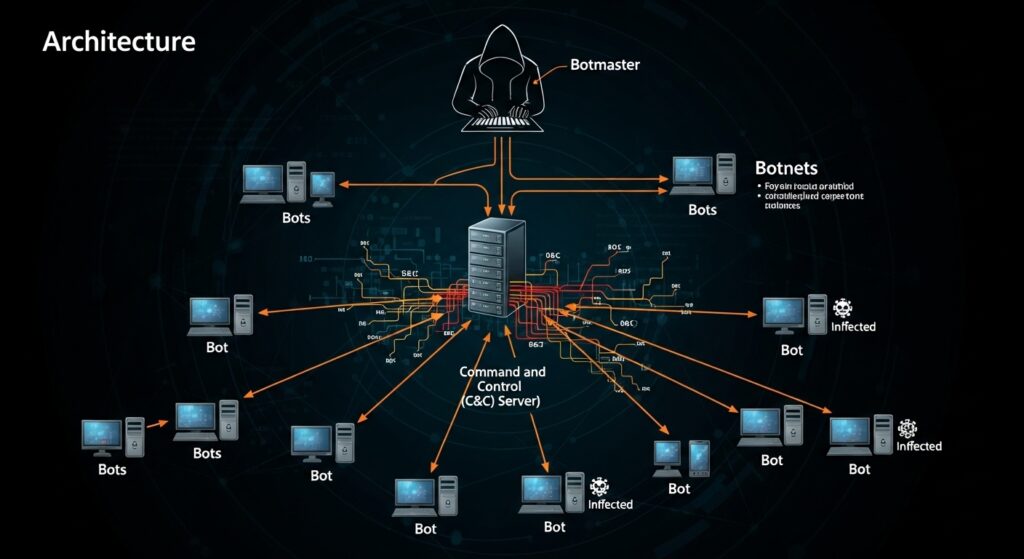
☣️ How Does a Device Become a Bot?
A device typically becomes part of a botnet without the user’s knowledge. The most common infection methods include:
- 📧 Phishing Emails: Clicking a malicious link or opening an infected attachment (like a Word document or PDF) in a spam email. This was the primary method used by the Emotet botnet.
- 🖥️ Drive-By Downloads: Simply visiting a compromised website can secretly download and install the malware onto your device.
- 🐎 Trojan Horses: The malware is disguised as legitimate software, like a free game, utility, or even an antivirus program.
- 🔓 Exploiting Vulnerabilities: The botmaster scans the internet for devices with unpatched software, old operating systems, or open security holes and injects the malware directly.
- 🔑 Weak Passwords: This is especially common for Internet of Things (IoT) devices. The Mirai botnet grew by scanning for devices (like cameras and routers) that were still using their default factory passwords (e..g.,
admin/password).
💥 What are Botnets Used For? (The Attacks)
The power of a botnet comes from its massive scale. A botmaster can use their “zombie army” for many criminal activities, including:
- 🚫 Distributed Denial of Service (DDoS) Attacks: This is the most famous use. The botmaster commands every bot in the network to flood a single target (like a website, an online game server, or a government service) with junk internet traffic. The target server is so overwhelmed by the millions of requests that it crashes and becomes inaccessible to legitimate users.
- ✉️ Spam and Phishing Campaigns: A botnet can send out billions of spam emails from all its infected devices. This makes the spam hard to block, as it comes from thousands of different IP addresses.
- 💳 Financial and Data Theft: Bots can be commanded to steal sensitive information. They can install keyloggers (to capture your passwords and credit card numbers), scan your computer for banking details, or steal your email contact lists.
- 📦 Spreading Other Malware: This is known as “Malware-as-a-Service.” The botmaster rents out their botnet to other criminals. For a fee, they will use their botnet to install other dangerous malware, such as:
- Ransomware: Encrypts all your files and demands a ransom payment.
- Banking Trojans: Specifically designed to steal online banking logins.
- 💰 Cryptojacking (Cryptocurrency Mining): The botnet uses the combined processing power (CPU/GPU) of all the infected computers to “mine” cryptocurrencies like Bitcoin for the botmaster. This makes the owner’s computer extremely slow and increases their electricity bill.
🛡️ How to Protect Yourself
- 🧬 Keep Antivirus/Anti-Malware Updated: This is your best defense. Install a reputable security suite and ensure it updates its definitions automatically.
- 🔄 Update Everything: Keep your operating system (Windows, macOS), your web browser, and all other software patched and up-to-date.
- 🎣 Be Skeptical of Emails: Never click on links or open attachments in unsolicited emails, even if they look legitimate.
- 🔒 Use Strong, Unique Passwords: Do not use default passwords, especially on routers and smart (IoT) devices. Use a password manager to create and store complex passwords.
- 🧱 Use a Firewall: A firewall acts as a barrier between your computer and the internet, and can often block unauthorized communication from a bot.
Mirai botnet attack
A major real-world example is the Mirai botnet attack that occurred in October 2016.
This botnet was responsible for one of the largest Distributed Denial of Service (DDoS) attacks ever recorded, which shut down major parts of the internet, primarily in the United States and Europe.
🎯 The Target: Dyn (A DNS Provider)
The botnet didn’t attack websites like Twitter or Netflix directly. Instead, it attacked their Domain Name System (DNS) provider, Dyn.
Think of DNS as the “phonebook of the internet.” When you type www.netflix.com into your browser, your computer asks a DNS provider (like Dyn) for the correct IP address (a string of numbers) to connect to.
By overwhelming Dyn with traffic, the Mirai botnet made it impossible for people to look up the “phone numbers” for major websites. The result: sites like Twitter, Netflix, Reddit, GitHub, Spotify, and The New York Times were inaccessible for hours.
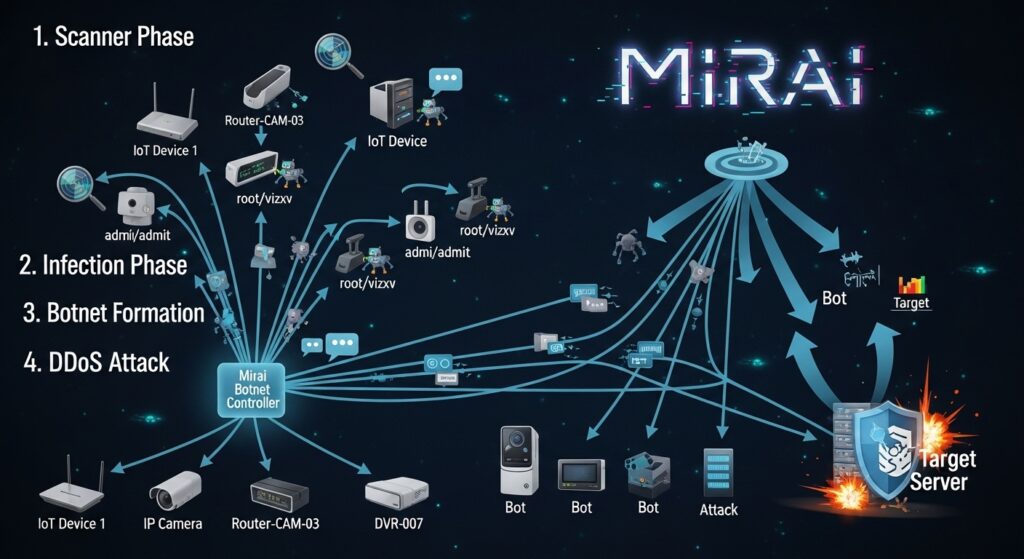
🧟 How the Mirai Botnet Worked
What made Mirai so powerful and unique was what it used for its “zombie” army.
- Bots: Instead of just infecting computers, Mirai scanned the internet for insecure Internet of Things (IoT) devices.
- Infection: It specifically looked for devices like home routers, security cameras, and DVRs that were still using their default, factory-set usernames and passwords (like
admin/password). - The Botnet: The malware would log in, infect the device, and add it to the botnet. This created a massive, distributed army of hundreds of thousands of hijacked IoT devices, all controlled by a single botmaster.
- The Attack: The botmaster then directed this army to flood Dyn’s servers with so much junk traffic that they couldn’t respond to legitimate requests, causing the massive outage.
Emotet
While Mirai was famous for its massive DDoS attacks using IoT devices, Emotet became infamous as one of the world’s most dangerous and costly botnets, specializing in financial theft and distributing other malware.
It was often described by law enforcement as a “Malware-as-a-Service” (MaaS) platform.
🎯 The Primary Goal: Malware Delivery
Unlike Mirai, Emotet’s main purpose wasn’t to crash websites. Its goal was to infect as many computers as possible (primarily targeting businesses and government organizations) and then use that access for two things:
- Steal financial information: It would scan computers for banking credentials, usernames, passwords, and other sensitive data.
- Rent out access: The botnet’s controllers would sell access to their network of infected computers to other cybercriminals.
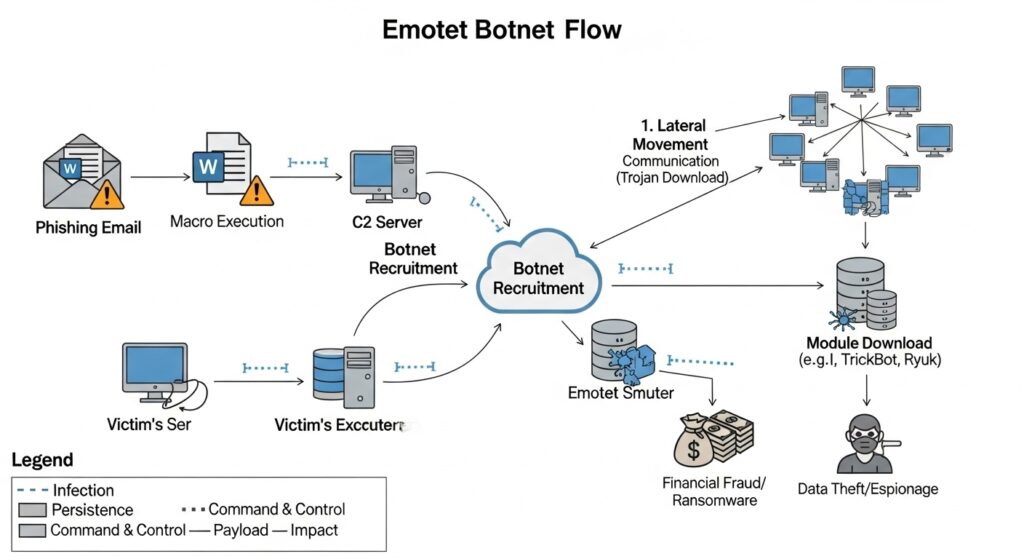
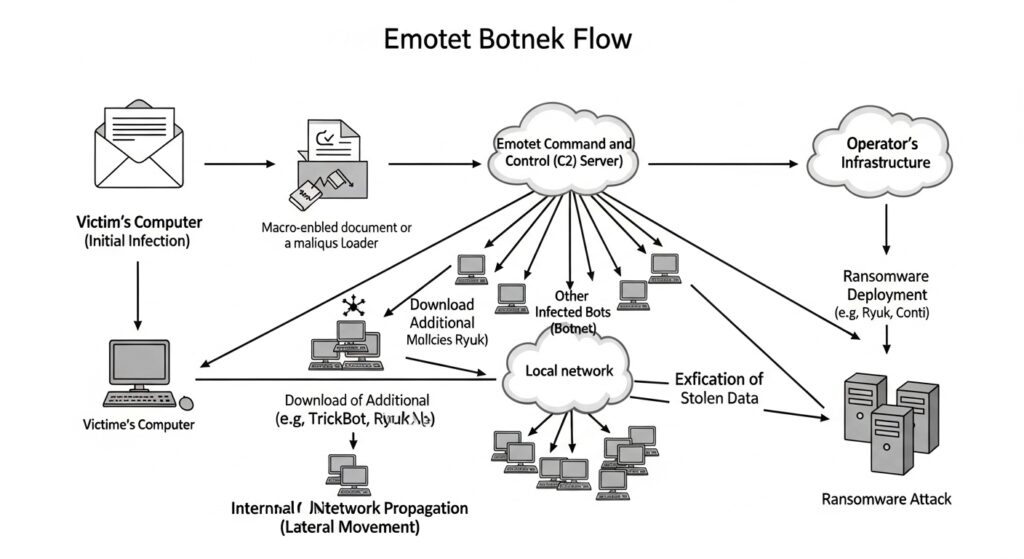
🧟 How the Emotet Botnet Worked
Emotet was a sophisticated, multi-stage operation:
- Infection (The Lure): The attack almost always began with a spam phishing email. These emails were often very convincing, appearing to be invoices, shipping notifications, payment details, or even COVID-19 safety information.
- The Payload: The email would contain a malicious link or an attached document (like a Word file or PDF). When a user opened the attachment and enabled macros (often prompted by a “please enable content” message), the Emotet malware would secretly install itself.
- The Botnet: The newly infected computer became a “zombie” in the Emotet network. It would immediately scan the user’s email contacts and start sending out more phishing emails to those contacts, making the infection spread rapidly.
- The “Service”: This is what made Emotet so destructive. Once a computer or network was compromised, Emotet would download other malware for its “customers,” including:
- Banking Trojans (like TrickBot): These would capture online banking logins to steal money directly.
- Ransomware (like Ryuk): This was the devastating final step. The criminals would use Emotet to deploy ransomware that encrypted an organization’s entire network, demanding hundreds of thousands or even millions of dollars in ransom.
In January 2021, a massive international law enforcement operation successfully took down Emotet’s infrastructure. However, its modular and resilient nature means that similar threats continue to emerge, modeled on its “Malware-as-a-Service” blueprint.